We
believe
you should have access to and control of your own data online.
the tools you use should empower you to share data without fear.
That’s why the Mainframe platform builds on five fundamental principles
Encryption
Your Content Can't Be Opened
Each Mainframe node has an asymmetric key pair associated with it. These keys are used to decrypt data intended for this node. When one node wishes to send data to another, it encrypts the data using the public key of the intended recipient node. This public key is obtained from a prior exchange of contact information that occurs out-of-band, such as by consulting a directory of contacts, or from a direct exchange of public keys between individuals. Packet encryption is part of Mainframe's transport protocols and cannot be circumvented.
For messaging, when data is being shared in a group setting, it must be encrypted in a way that prevents would-be eavesdroppers from gleaning content or identifying the group participants. Although it is possible for the sender to encrypt the message separately for each recipient, this results in significant CPU and network loads as the number of participants in the group increases. Mainframe provides protocols for group shared key negotiation so that group participants can send encrypted messages more efficiently to one another.
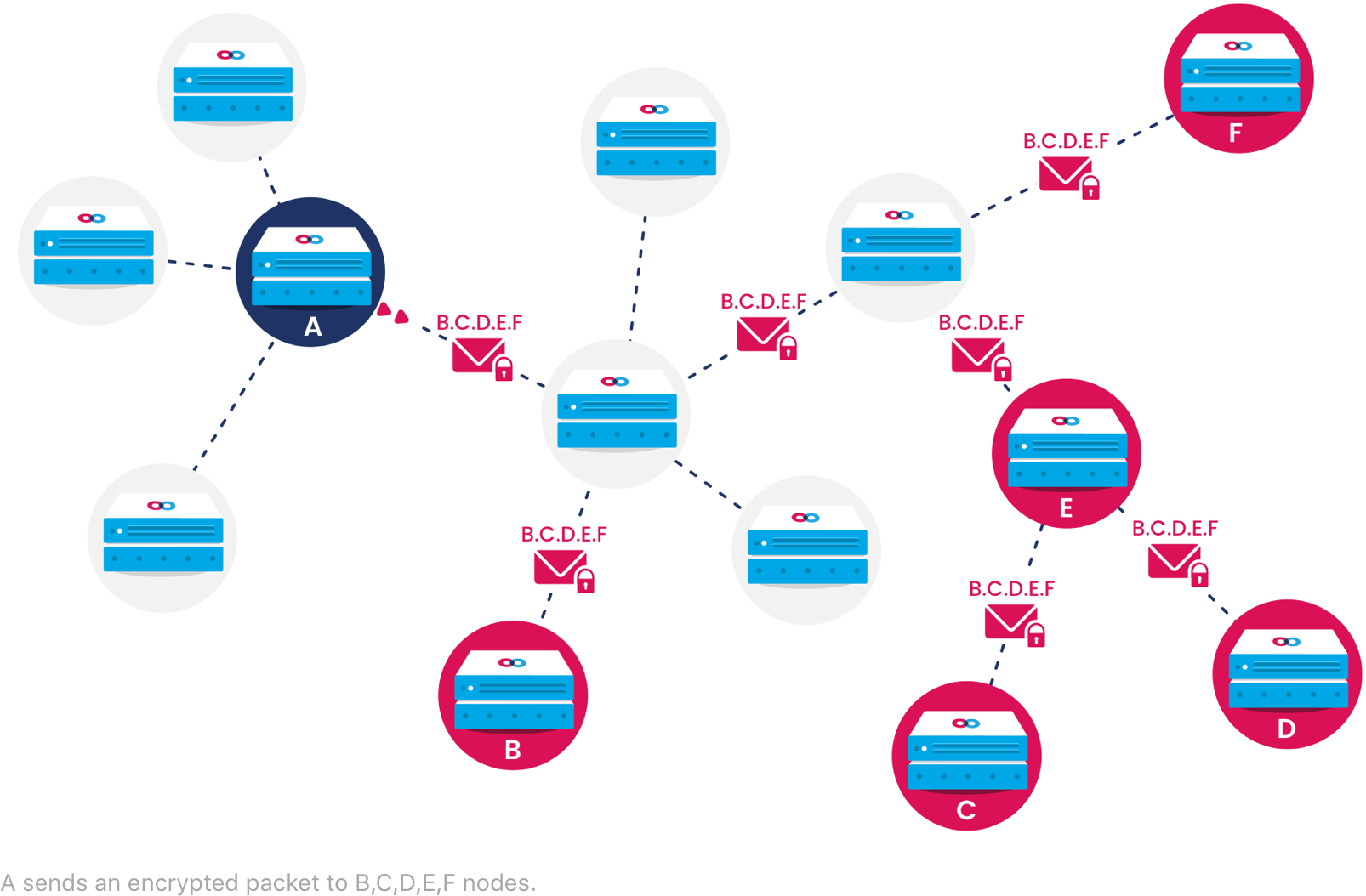
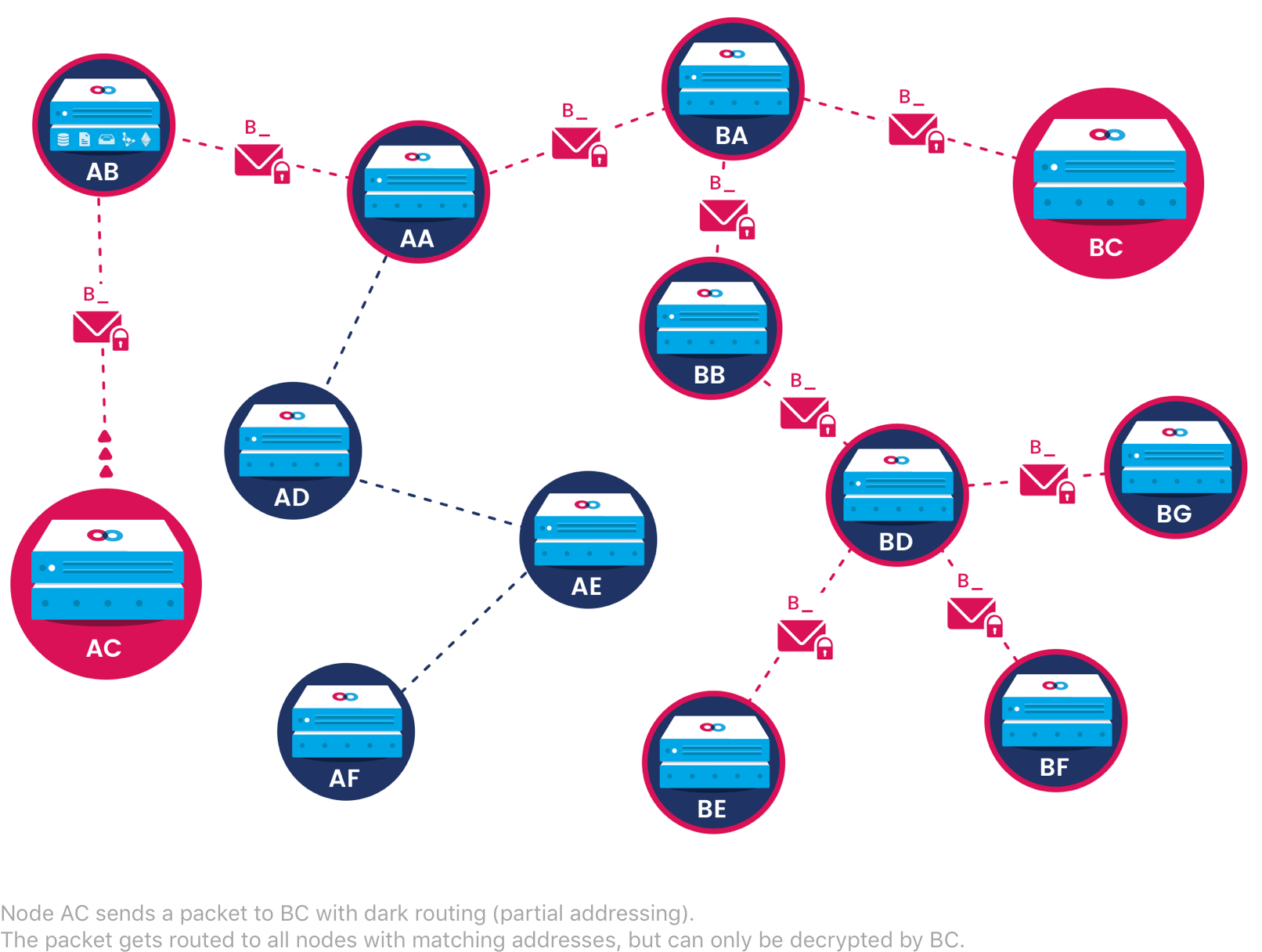
Dark Routing
Your Content Can't Be Followed
Despite their use of encryption, conventional applications still allow malicious actors to glean information about who is communicating with whom. Mainframe allows users to prevent this using configurable dark routing. Applications are able to select the appropriate level of specificity when addressing data packets to other nodes. Too much specificity increases the possibility that malicious actors could identify communication, while too little delays data transmission and increases transmission costs. Mainframe algorithmically determines sensible default routing settings based on network conditions and users' privacy requirements.
Because data packets do not need to be fully addressed, nodes must have another means of identifying messages they are interested in viewing. For messaging applications, this is done using topic IDs. When a peer-to-peer or group discussion is initiated, a topic ID is selected at random and shared privately with all participants, who then listen for future messages with the same topic ID. Even if nodes select a topic ID that is already being used by other nodes, they will only be able to decrypt messages from group members who have the previously agreed-upon shared key and will ignore other messages in the topic, so topic IDs help nodes reduce processing overload for irrelevant messages but gracefully handle collisions.
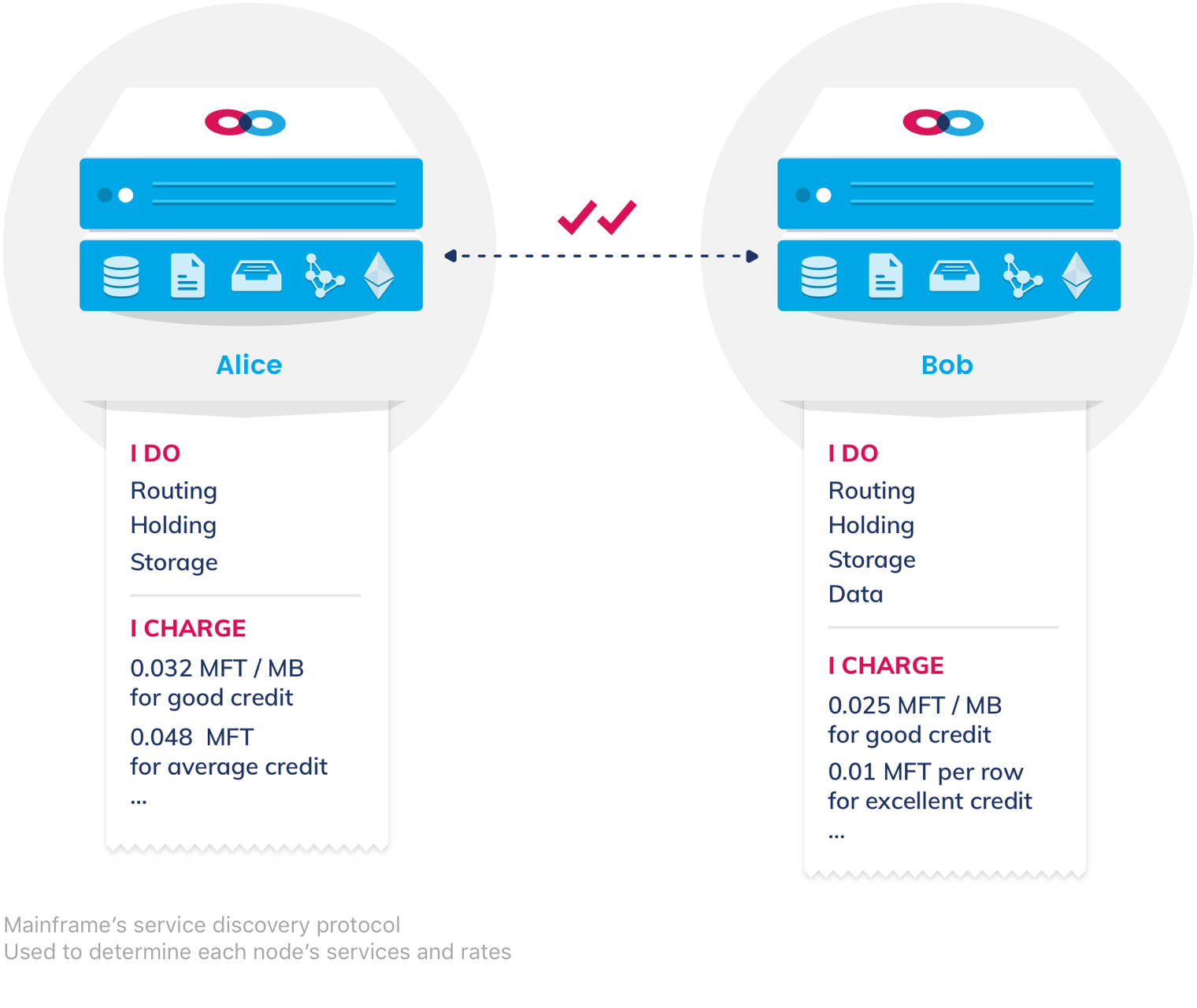
Incentivization
The Network Can't Die
Mainframe communications make use of a generalized model for incentivized service provision called `"Swap, Swear, and Swindle." This model is used to incentivize packet routing, packet holding, file storage, and database storage, and other application services, while optimizing for bandwidth requirements and associated cost.
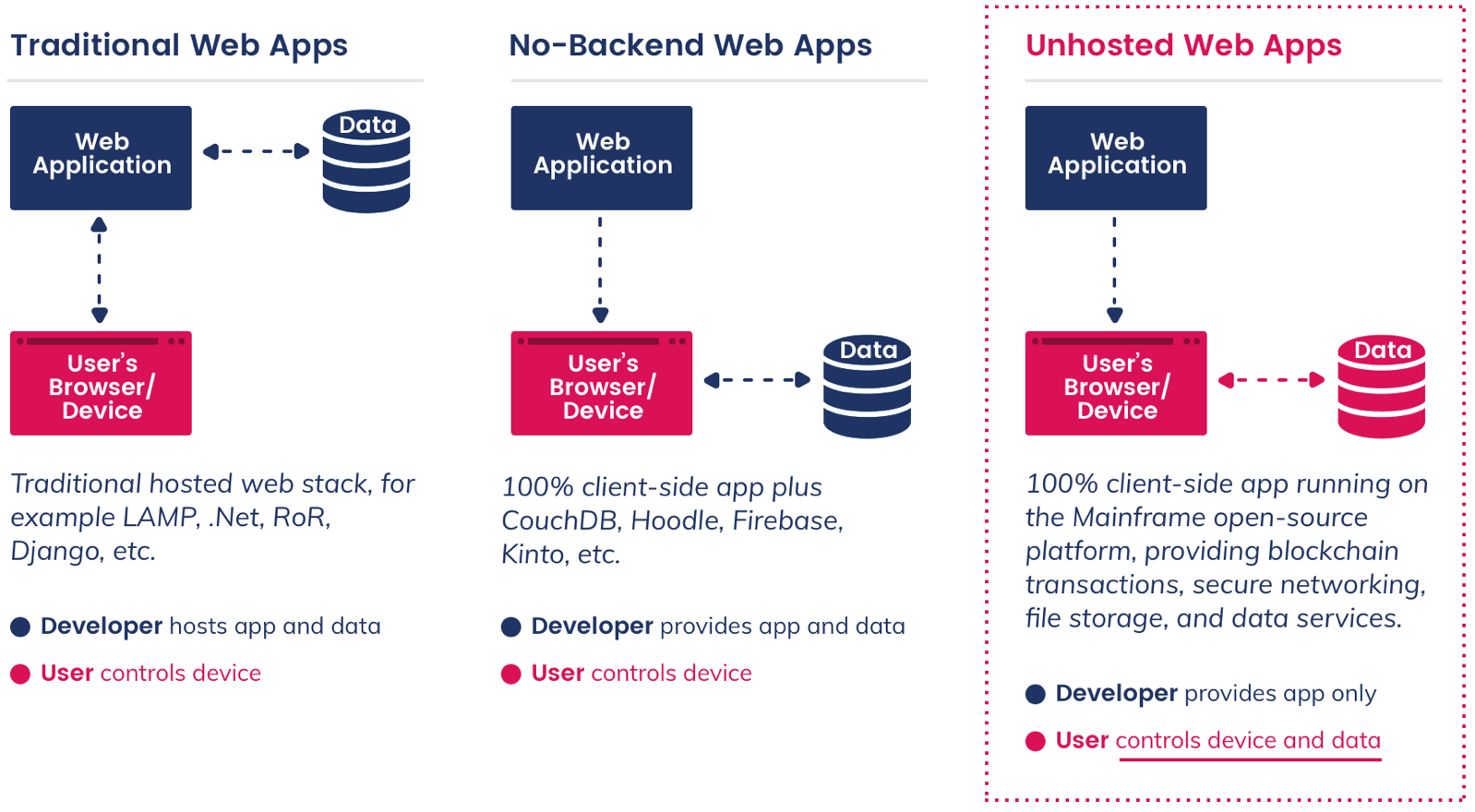
Peer-to-Peer Architecture
The Network Can't Be Shut Down
Decentralized data services will allow application data to be stored in a secure distributed fashion throughout the blockchain network without reliance on any infrastructure, including self-deployed cloud services for data storage. Blockchain nodes will be able to request that data be stored on their behalf while they are disconnected, for a fee. Nodes can also incentivize the storage of data or files, the processing of asynchronous tasks, the routing of messages, or the management of payments, all with Mainframe tokens.