Dark Routing
Your Content Can't Be Followed
Despite their use of encryption, conventional networking systems still allow malicious actors to glean information about who is communicating with whom. Mainframe allows nodes to prevent this using configurable dark routing based on Holbrook's work on the PSS protocol1 which is itself an evolution of the Whisper protocol, originally conceived by Wood.2 In dark routing mode, packets are routed to each node whose address matches the partially disclosed destination address, moving efficiently towards this subset of nodes, but after that they are distributed to all matching nodes, making it intractable for any network observer to infer the intended recipient within that zone.
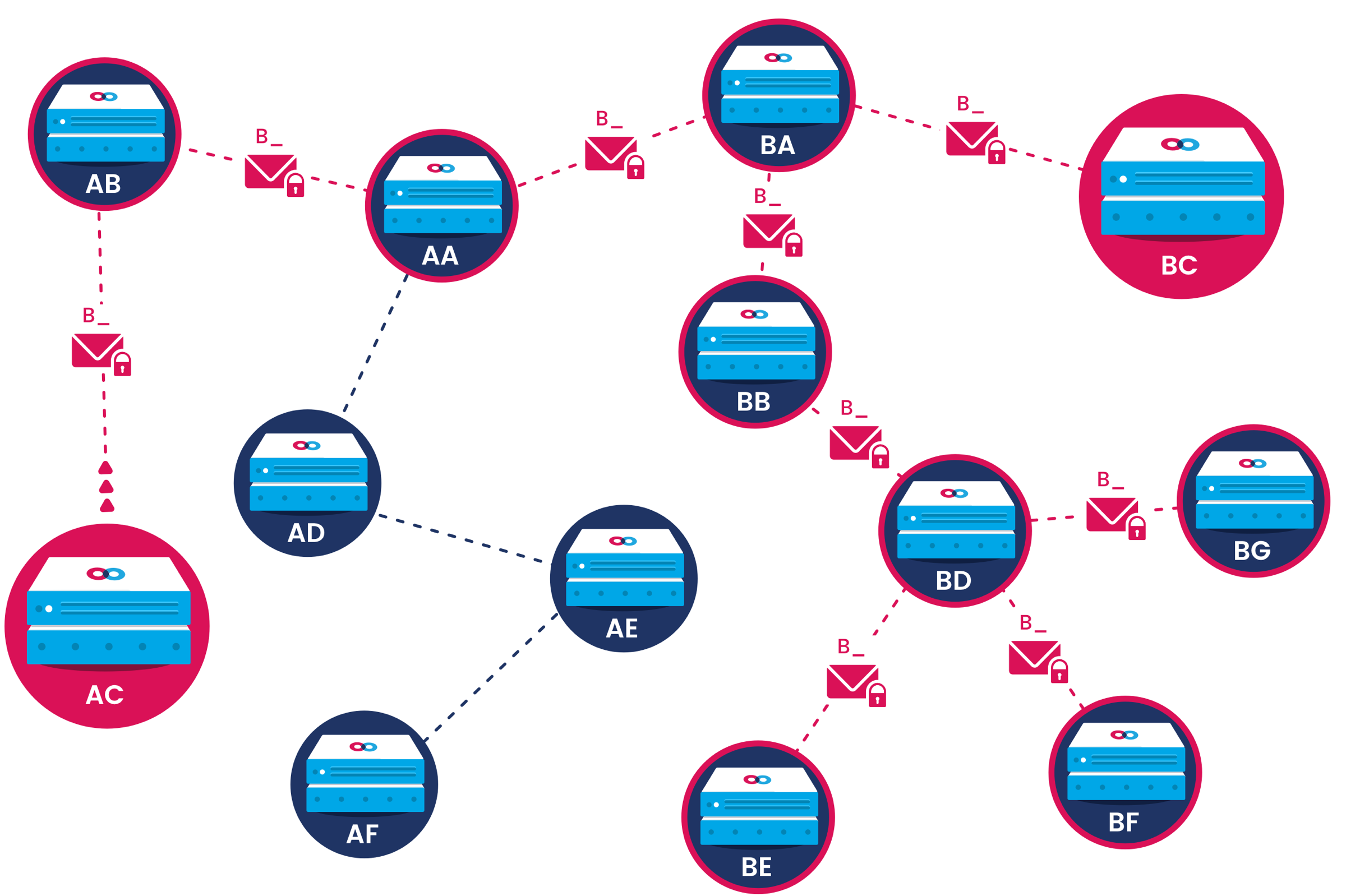 Node AC sends a packet to BC with dark routing (partial addressing).
Node AC sends a packet to BC with dark routing (partial addressing).The packet gets routed to all nodes with matching addresses, but can only be decrypted by BC.
Nodes are responsible for selecting the appropriate level of luminosity (address specificity) when addressing packets. Too much luminosity increases the possibility that malicious actors could identify patterns of communication between nodes, while too little increases congestion and transmission costs. Mainframe provides algorithms for determining sensible luminosity settings based on network conditions and privacy requirements for different use cases.
Because packets do not need to be fully addressed, session management becomes more challenging. Nodes must have another means of identifying packets they are interested in viewing. This is done using a previously agreed-upon topic ID inside a packet. Mainframe provides session management protocols that help applications keep track of and initiate separate data streams. When a new session is negotiated between nodes or groups of nodes, a topic ID is generated and shared privately with all session participants, who then listen for future packets with the same topic ID.
Even if nodes select a topic ID that is already being used by other nodes, they will only be able to decrypt packets that have been encrypted with a known secret key, and will ignore other packets having the same topic ID, so topic IDs help nodes reduce processing overload for irrelevant packets but gracefully handle collisions. When multiple, disparate communication streams use the same topic ID, it also helps to make it more difficult for would-be eavesdroppers to recognize communication patterns.